Information Security Interview Questions for entry and mid level
For any given application about 118 people will apply and 22% of applicants will be selected for the interview. Of that 22% only 1, maybe 2 or 3 people will be given a job offer depending on how many positions are open. To give yourself the best chance to be successful, preparation is extremely important. Most interviews within information security will consist of similar types of questions, understanding what these questions are and how to answer them will give you the best chance to impress the interviewer and get the job.
How to answer Interview questions

For answering interview questions I recommend the star methodology. It’s a framework for answering any questions relating to a past experience. It stands for situation, task, action and result. Whenever you are asked a question such as “Tell me about a time when you did …..”, it helps to organize your thoughts by thinking about those four elements. Begin with describing the situation you were in. This includes what the problem was, how many people were involved, how many clients, executives or senior management that needed help etc. Then explain the details of the task that you were assigned. Follow this by explaining the actions that you took to complete this task, then highlight how those actions lead to a successful resolution of the problem. By highlighting all four of these points you will give the interviewer a clear picture of the situation.
25 Information Security Interview Questions
1) What is the difference between a threat, vulnerability and a risk?
A vulnerability is a weakness in a system or program. A threat is an entity that tries to exploit the vulnerabilities in a system and a risk is the potential loss, damage or destruction of an asset as a result of a threat exploiting a vulnerability.
2) How do you protect a server?
This process is called system hardening and it’s all about making a server as secure as possible. This is your chance to demonstrate your understanding of what causes hacks and how to stop them. Some of the points you want to hit are: closing unnecessary ports, having firewall rules, change default passwords, remove unnecessary services, apply all relevant security patches, enable encryption, create data backups and setup system monitoring.
3) What is a firewall?
A firewall is a security device that filters incoming and outgoing traffic. It decides whether to block or allow specific traffic based on a defined set of rules.
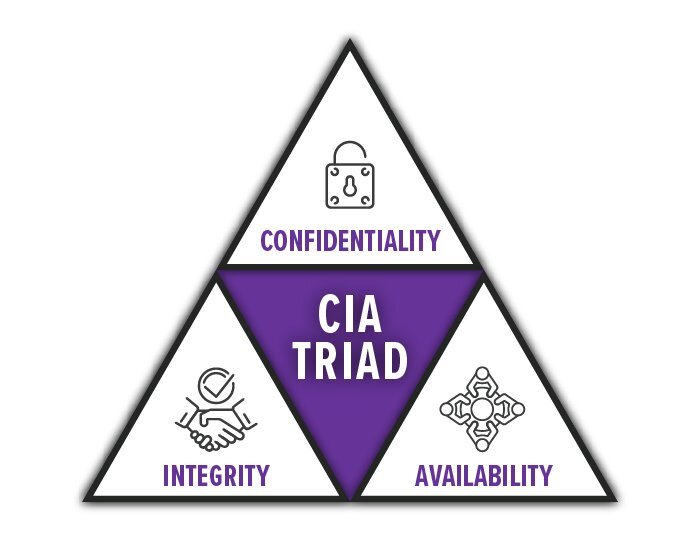
4) What is the CIA triad?
The CIA triad is confidentiality, integrity and availability. Confidentiality means to ensure only the authorized users have access to information. Integrity means to protect information from unauthorized modifications. Availability means to ensure that information is available to users whenever they request the service.
5) What is Regulatory Compliance?
Regulatory compliance means adhering to the laws and regulations that are mandated by the government or an industry regulatory body.
6) What is the difference between encoding, encryption and hashing?
Encoding is a reversible transformation of data that is used to make data usable on different types of systems, it helps with availability. Encryption is a reversible type of data transformation that is considered secure because it requires the use of keys in order to decrypt the data, it protects confidentiality. Hashing is a one-way summary of data that cannot be reversed and is used to prove integrity.
7) What are some common Indicators of compromise for identifying a compromised system?
Some common signs of infection are slow performance, high memory usage, lack of storage space, unexpected pop ups and your system unexpectedly shutting down.
8) What is cross-site scripting(XSS)? And how to defend against it?
Cross site scripting is a client-side code injection attack. This is when an attacker injects code into a legitimate web page or web application. Once someone visits that page, it will execute the code. To prevent it, the website or web application must sanitize the input. Sanitization means whenever you accept information from the user through a web form or other means, it must be checked for malicious code.
9) What is the difference between UDP and TCP?
TCP is a connection oriented protocol that checks for errors and guarantees delivery of data while UDP is connectionless and doesn’t check for errors. TCP is more reliable but much slower than UDP.
10) DDOS and potential mitigation?
A distributed denial of service (DDOS) attack is an attempt to disrupt normal traffic by spamming a device with unsolicited traffic until the machine can’t respond to legitimate traffic. Some common ways of mitigating ddos is to use packet filtering devices like firewalls, blocking IP addresses that are spamming you, getting ddos protection as a service or redirecting the traffic (sinkholing).
11) What is a WAF and what are the types?
A web application firewall (WAF) is a device that protects web applications by filtering and monitoring HTTP traffic between a web application and the internet. You can have network-based web application firewalls (NWAF), host based web application firewall (HWAF) and cloud based web application firewall (CWAF).
12) How does a ping work?
The ping tool is used to test whether a host is reachable over a network. It works by sending a request to that machine and if that machine responds by sending back a data packet, we know that machine can be accessed.
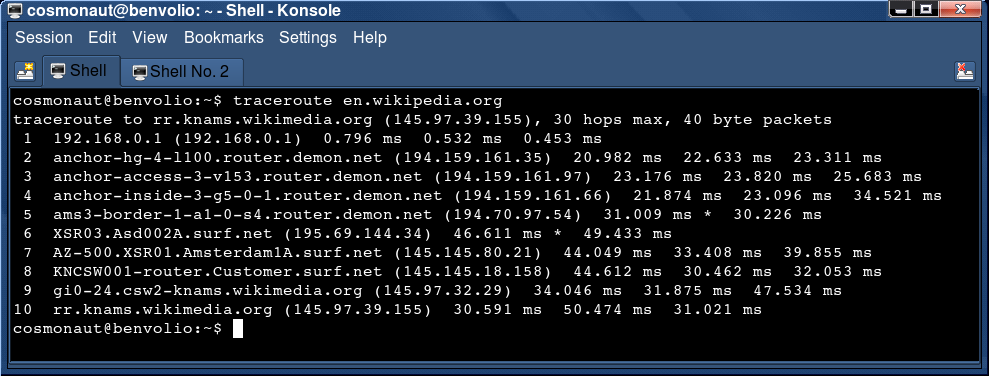
13) What is traceroute/tracert?
Traceroute is a tool used to track the pathway a data packet took from source to destination (hops). It shows the IP addresses of each hop, provides time intervals and is often used to troubleshoot connectivity issues.
14) What security blogs or podcasts do you follow?
Staying up to date with news in security is very important. There are consistently new vulnerabilities being announced, new patches, potential vendor breaches and many other elements that require you to be aware of what’s going on. If you don’t follow any podcasts you can find some here.
15) What is HTTPS, SSL and TLS?
HTTPS is a secure version of HTTP, the protocol used to send data between a web browser and a website. SSL stands for secure sockets layer, it allows for authentication, encryption and decryption of data sent over the internet. TLS is an updated, more secure version of SSL.
16) Difference between processes, policy and guidelines
A process is a set of actions taken to achieve a specific task. A policy is a set of rules that staff abide by as they carry out their day to day work, it is required to follow policy. Guidelines are a set of recommendations or best practices for completing a task, but they are not required.
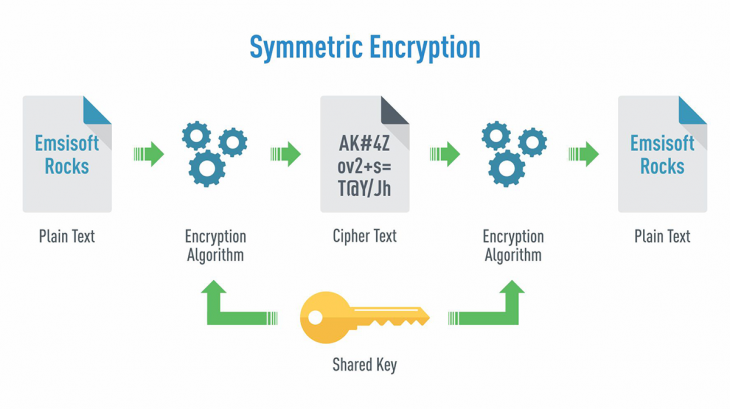
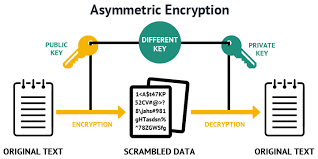
17) What’s the difference between asymmetric and symmetric encryption?
Symmetric encryption uses one key (a shared key) for both encryption and decryption. While asymmetric encryption uses two keys, one for encryption (public key) and another for decryption (private key).
18) What is SSH and how is it used?
Secure Shell (SSH) is a remote administration protocol that allows users to connect to servers over the Internet. Essentially, you can open a terminal on your computer, input commands and have that run on the remote server as if you were typing the commands directly on that server.
19) What is salting and peppering a hash?
A salt is a random value that is passed to the hashed version of a password. It prevents people from guessing the hash value if they know the hash algorithm you used. A pepper is a random value added to a password before the hashing process.
20) What are the four ways to authenticate someone?
You can authenticate someone with something they know (password), something they have (ID card), something they are (face scan or fingerprint) or something they do (the way they walk or talk).
21) What is the difference between a HIDS and NIDS
A host based intrusion detection system (HIDS) monitors an individual system for any signs of intrusion. While a network based intrusion detection system (NIDS) monitors the traffic across the network for any sign of malicious activity.
22) What is the difference between a false positive and false negative and which is worse?
A false positive is when an alert is created for an activity that is not malicious, while a false negative is when there is no alert generated for an activity that is malicious. A false negative is worse because that means that malicious activity is going undetected, while a false positive is just more of an inconvenience.
23) What is the difference between a black box test and a white box test
A white box test is when an application or system is tested with all of the knowledge of the internal workings of a system. A black box text is when no internal knowledge of the system is provided to the testers, they perform the test with the same level of knowledge that an attacker outside of the company would have.
24) Do you have any questions?
Always take this opportunity to find out more about the job. Find out how the role became available, the size of the team, what you would be doing on a day to day or weekly basis or any other questions you have. The only thing you may want to refrain from asking about is salary, that typically should be saved until you know that they are interested in hiring you.
25) What made you apply for this position?
Usually companies are looking to see if you’re a good fit based on what you’re looking for in your career. You can use this as a chance to explain why you would be a good fit for this position if your skillset and experience aligns really well with the job posting. If you’re looking to stay in the company for a long period of time, this is also a good time to mention that and explain why you would be a good bet for the company.Shimon Brathwaite
Shimon Brathwaite is a cybersecurity professional, Consultant, and Author at securitymadesimple. He is a graduate of Ryerson University in Toronto, Canada. He has worked in several financial institutions in security-related roles, as a consultant in incident response and is a published author with a book on cybersecurity law. My professional certifications include Security+, CEH and AWS Security Specialist. You can contact me here.



