IoT Devices in the Workplace: Security Risks and Threats to BYOD Environments
As well as transforming myriad homes and various industries, the internet of things (IoT) has been reshaping enterprises. And one of the most apparent manifestations of how the IoT has prompted changes in businesses and organizations is the presence and use of employee-owned IoT devices in the workplace.

Gone are the days when, in accordance with the practice known as BYOD (bring your own device), employees would bring only their laptops, tablets, or smartphones to work and connect them to the office network primarily to aid them in their tasks. Now, employees are apt to also bring their personal IoT devices so as to be able to continue using them even while at work. These include wearables like smartwatches and fitness trackers, entertainment devices such as e-readers and game consoles, and even portable appliances such as smart coffee makers and printers.
But the influx of such IoT devices in the workplace poses a new set of challenges for enterprises, particularly their security teams. Already, security teams are tasked with ensuring the protection of employee-owned laptops, tablets, and smartphones — the main, if not the only, devices in the BYOD norm of old — along with actual company assets. Under the new normal, they also have to contend with risks and threats that arise from the increasing prevalence of miscellaneous consumer-grade IoT devices within enterprise premises. This is especially true considering that instances of compromise involving IoT devices have emphasized how these technological conveniences have attendant security concerns that not all companies may be immediately prepared for.
Companies’ established BYOD policies and procedures play a big role in preventing unauthorized access and otherwise defending business assets. But as more and more employees opt to bring their IoT devices to work, these will have to adapt to the changes in the IoT security landscape. Short of revoking BYOD privileges, enterprises should therefore update their BYOD programs. To that end, this guide recommends best practices in thwarting some of the most prevalent risks and threats involving IoT devices in BYOD environments.
[Read: National Cyber Security Awareness Month: The enterprise’s safety online is everyone’s business]
Vulnerabilities
Taking advantage of device vulnerabilities has long been a popular tactic among threat actors, and it is no different with IoT devices. In fact, some of the most damaging IoT device-related incidents that made headlines over the years resulted from the exploitation of vulnerabilities. And in many instances, there had been available fixes for the flaws in question. Indeed, negligence in applying patches to affected devices is an issue that enterprises need to deal with, especially since vulnerabilities can allow attackers to make further movement beyond the devices and into company networks and assets.
Best practices: An onboarding procedure should be in place to enable employees to register their devices with the IT and security teams before the devices are allowed to connect to the enterprise network. In the enrollment process, all relevant device and system information should be logged and proper device security settings should be configured, among other key steps. A continuous awareness program is also recommended to remind employees to regularly install patches and updates from legitimate vendors and developers for their respective devices.
[Read: Mapping the Future: Dealing With Pervasive and Persistent Threats]
Hacking
IoT devices in BYOD environments — be they smartwatches, smart health trackers, smart speakers, or smart yoga mats — are brought in by employees to make more or less uninterrupted use of their special features. But hackers can take advantage of these functionalities to get through the enterprise network, especially given the often minimal security measures in place for the devices. Access to the company network can allow attackers to carry out their malicious activities: scanning for other vulnerable devices, sniffing for data, stealing stored information, accessing servers and systems, and turning devices into parts of botnets, among others.
Best practices: Employees should be encouraged to familiarize themselves with the specific features of their IoT devices, especially for possible hidden features or components. Further, aside from requiring employees to have their personal devices duly enrolled, the company should set up a network, separate from the one used for actual operations, to which these devices should be connected. It should also adopt a multilayered security solution that can detect and block malicious activities and attacks from networks to endpoints.
[Read: 2018 Mobile Threat Landscape]
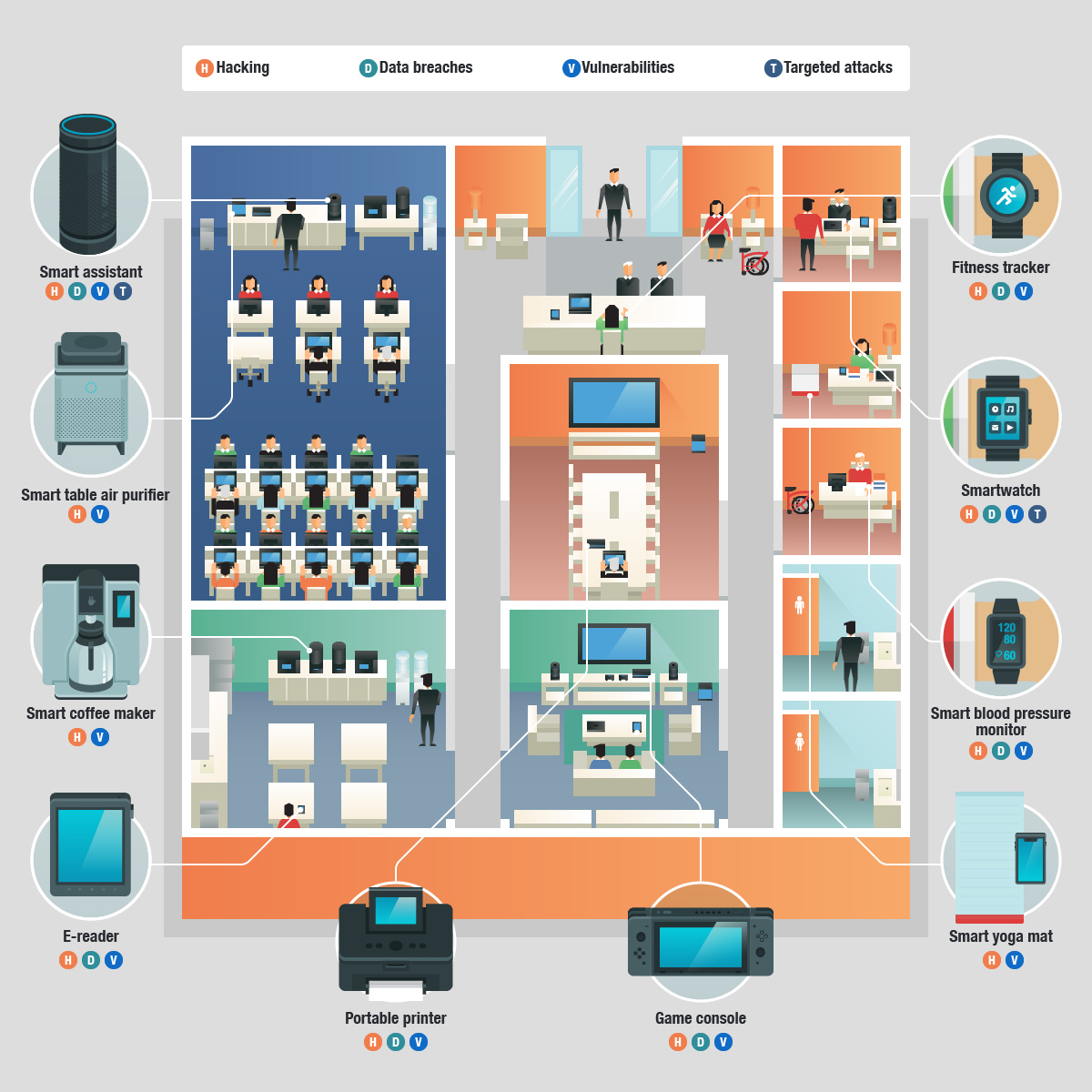
Risks and threats arising from the increasing prevalence of IoT devices in BYOD environments
Targeted attacks
A simple online search can show a multitude of exposed devices connected to the internet, such as smartwatches and smart speakers, along with associated systems that may likewise be exposed. This is troubling in that attackers have been known to choose an exposed device, note the device’s unique system information, and assess the vulnerabilities of the device and the system it is connected to so as to facilitate targeted attacks. With just a cursory online search to go on, malicious actors can use a variety of techniques to access and cause damage to the target company’s network and assets.
Best practices: Enterprises should consider using websites and services like Shodan and WhatsMyIP as tools to aid in scanning their networks for exposed devices, open ports, and other threat vectors — and should execute the necessary actions against any discovered lapses in security. They should also implement awareness programs and learning courses to promote a security-first mindset among employees, including preventive measures against device exposure.
[Read: How attackers are abusing high-profile users and executives]
Data breaches
As likely as it is for an ordinary watch to be lost or stolen, it is just as probable for a smartwatch to meet the same fate. But in the case of the latter, there is the risk of information leakage or data exfiltration, which may involve sensitive company information and data stored in email and memo apps, for example — especially if the smartwatch was being used in a BYOD environment. Lost or stolen devices are another important BYOD security consideration since the information or data they contain can be used by threat actors to carry out sabotage or espionage, among other malicious motivations. Device loss and theft contribute to the occurrence of large data breaches (including unintentional disclosures), making them a major concern for enterprises with BYOD programs — a 2012 Trend Micro study found that nearly half of the surveyed enterprises that allowed employees to connect personal devices to their networks had experienced some form of data breach.
Best practices: IT and security teams should recommend device security settings to enable, and review their network access and storage settings at regular intervals. This allows them to go over and customize their security for stricter implementation of information access according to business requirements — especially in consideration of the need for compliance with legal mandates and international regulations pertaining to data privacy and protection. For their part, employees should be urged to inform the IT and security teams of the devices they bring to the workplace, and to use available multifactor authentication and data encryption features on their devices. They should also notify the IT and security teams when any of their devices is lost or stolen. Aside from reinforcing the security team’s ability to monitor, detect, and block threats and attacks before they hit the enterprise, this helps in quickly determining the type of threat attempting intrusion, controlling leakage and loss, and pinpointing the device being used for attacks.
[Read: Uncovering the truth about corporate IoT security]
A culture of security awareness is of particular importance in environments that include employee-owned devices as well as company assets. It acquires even greater importance in light of the growing trend toward the use of consumer-grade IoT devices in the workplace. BYOD programs, therefore, should be reevaluated and reestablished in these environments. And this is a shared responsibility that is incumbent on enterprises and employees alike to undertake and fulfill: security integration from the conceptualization to the implementation of BYOD policies and procedures in line with the continuing expansion of the IoT.
Pay close attention to security aspects of your computer usage.
The best way to stop your information from being exposed is to have it properly protected. When it comes to networks, understanding exactly how to do it is required.
Become a Cyber Security Professional and Save $250 on upcoming CISSP, CEH, CHFI courses starting soon. The savings applies as well to additional Cyber Security courses such as Security+, CySA+, CASP, CCNA: Security, CCNP: Security, CISM, and more.
www.cedsolutions.com (800) 611-1840 info@cedsolutions.com



